Securing an enterprise network a decade ago was straightforward: build strong perimeter defenses, keep threats out, and trust everything inside. IT environments were largely on-premises, and security teams focused on fortifying the firewall, treating internal users and applications as inherently safe.
But technology, as always, changed the rules. The rapid adoption of cloud services, mobile devices, and remote work blurred traditional corporate perimeters. The once-reliable “castle-and-moat” approach — where a strong perimeter kept attackers at bay — became not just obsolete but a liability. A single compromised device or stolen user credential could grant hackers free rein to move laterally across an entire network.

Zero Trust Architecture or ZTA emerged as a response to this new reality. Instead of assuming trust based on network location, Zero Trust treats every request as potentially malicious, requiring continuous authentication and strict access controls. As Gaartner puts it, Zero Trust means removing implicit trust from infrastructure and continuously verifying identities, devices, and context before granting access — providing just-in-time, least-privilege permissions.
The concept isn’t new. Security experts have long advocated for a shift from perimeter-based models, dating back to the early 2000s with the Jericho Forum’s idea of “de-parameterization.” But Zero Trust gained mainstream attention when Google implemented its BeyondCorp framework in response to the 2009 Operation Aurora cyberattack. By 2020, the U.S. government established Zero Trust guidelines (NIST SP 800-207), requiring its implementation across federal agencies. Currently, organizations worldwide are adopting similar measures, realizing that in a cloud-first era, traditional defenses can and will be circumvented.
Core Principles and Best Practices of Zero Trust Architecture
At its core, Zero Trust is built on a few fundamental principles:
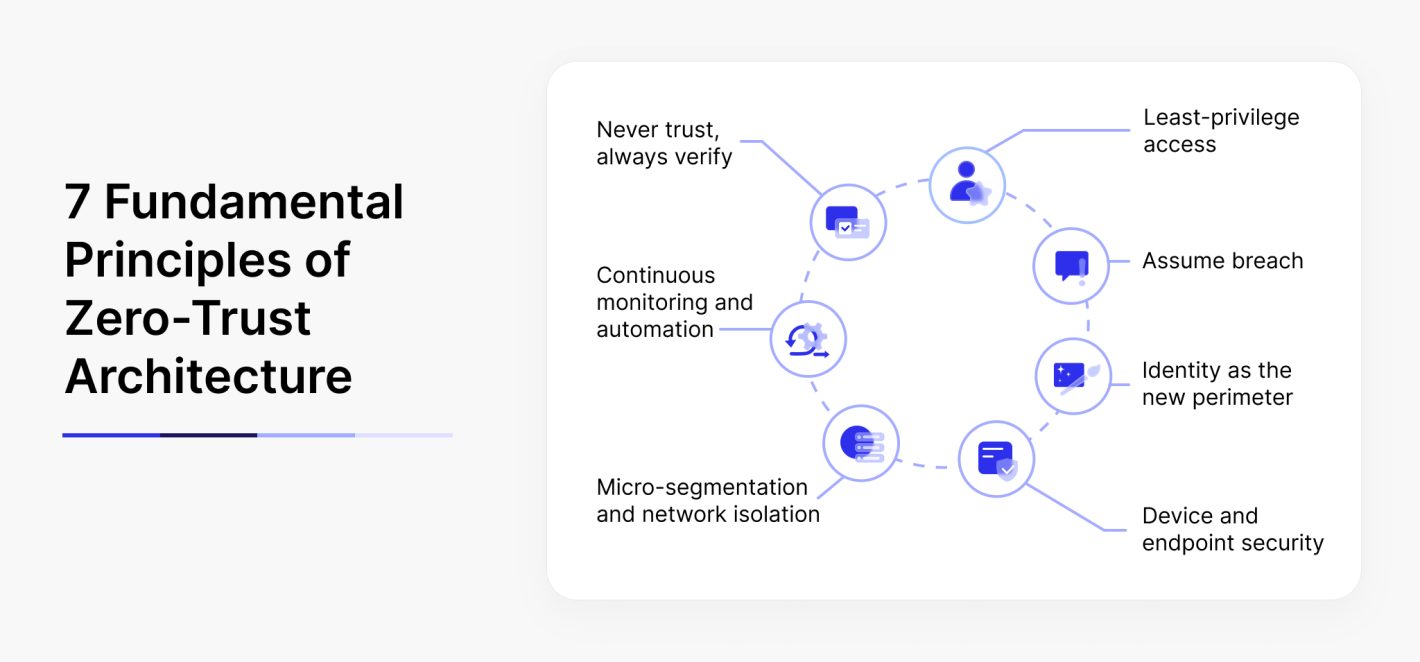
Zero-Trust architecture core principles
- Never Trust, Always Verify – Every request for access is authenticated and authorized in real-time, regardless of whether it originates inside or outside the network. This extends beyond basic credentials; security teams verify device health, location, behavioral patterns, and other risk factors before granting access. If anything seems off — such as a user logging in from an unusual location or a device missing security patches — access is denied or restricted.
- Least-Privilege Access – Users and systems receive only the minimum level of access necessary to perform their tasks. This principle is upheld through role-based access controls, micro-segmentation, and just-in-time permissions. Even if an account is compromised, the impact is limited because attackers cannot navigate freely across systems.
- Assume Breach – Zero Trust operates on the assumption that an attacker is already inside the network. Organizations continuously monitor activity, use behavioral analytics to detect anomalies and implement automated containment mechanisms. This “assume breach” mindset ensures that even if attackers gain access, their ability to cause harm is minimized.
- Identity as the New Perimeter – With employees, contractors, and cloud workloads accessing systems from any location, identity becomes the primary control for security. Multi-Factor Authentication or MFA, conditional access policies, and robust identity governance ensure that only authorized users gain entry. In cloud environments, even applications and services must verify their identity before communicating.
- Device and Endpoint Security – Every device is treated as potentially compromised until proven otherwise. Organizations enforce security policies that ensure only managed, up-to-date devices can access corporate resources. If a device falls out of compliance — such as missing critical patches — it is automatically quarantined until remediated.
- Micro-Segmentation and Network Isolation – Traditional networks are often flat, allowing attackers to move laterally once inside. Zero Trust replaces this model with micro-segmentation, where each application, database, or service is isolated behind strict access controls. Even within the same organization, departments or workloads cannot communicate unless explicitly permitted.
- Continuous Monitoring and Automation – Zero Trust generates a massive volume of security telemetry, from login attempts to network flows. Organizations can leverage AI-driven analytics to detect suspicious activity and automate response actions. For instance, if an employee’s account suddenly downloads an excessive amount of data, access is automatically revoked, and security teams are alerted.
Note, that these principles are not theoretical. They are already being implemented across industries to protect sensitive data and critical systems.
The Business Impact of Cloud Security Breaches
In this section, let’s answer the question: “Should you invest in approaches like ZTA?”. The reality is that high-profile cyberattacks continue to make headlines, underscoring the cost of inadequate security. In 2023, the average data breach cost reached $4.24 million, rising to nearly $5 million for organizations with remote workforces. Cloud-based breaches proved even more expensive, with incidents involving public cloud data averaging $5.17 million.
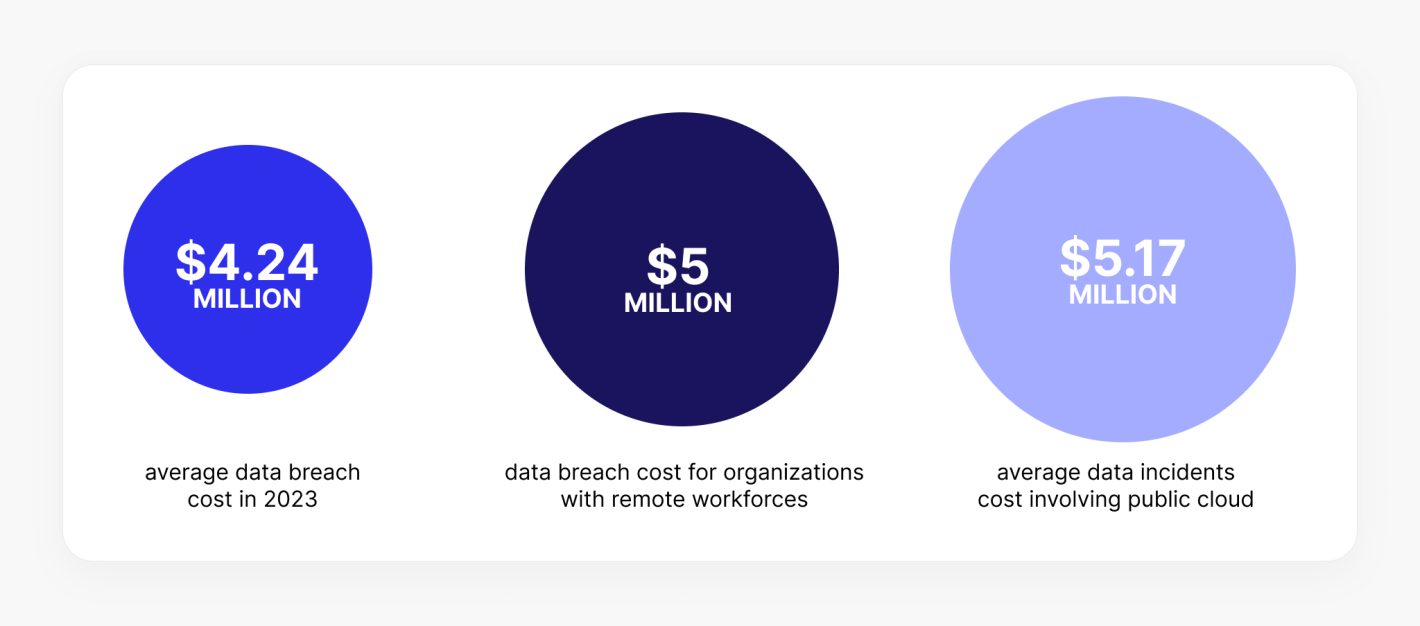
Source: Deloitte, IBM
But the financial impact goes far beyond immediate losses. Ransomware attacks can cripple operations, regulatory fines can reach hundreds of millions, and reputational damage can drive away customers. Take the 2019 Capital One breach, where a misconfigured cloud firewall exposed over 100 million customer records. The fallout included $270 million in total costs, including an $80 million fine and a $190 million class-action settlement.
Studies suggest that as much as 90% of the financial impact of a cyberattack is not immediately visible. This hidden toll can result in lost business, increased customer turnover, and soaring cyber insurance premiums. In regulated industries, a data breach can lead to government investigations, compliance penalties, and even legal liability for executives.

Source: The Council of Insurance Agents & Brokers
These stark realities have led business leaders to rethink security strategies. Finance executives, in particular, now see cybersecurity not as an IT issue but as a business-critical investment. The shift in mindset is clear: the cost of inaction far outweighs the investment in proactive measures like Zero Trust.
Zero Trust as a Strategic Advantage
While Zero Trust is often framed as a risk mitigation strategy, its benefits go beyond security — it’s also an enabler of digital transformation. According to Statista, 31% of organizations have adopted Zero Trust primarily because it is an “industry best practice. 27% are planning to implement it this year.
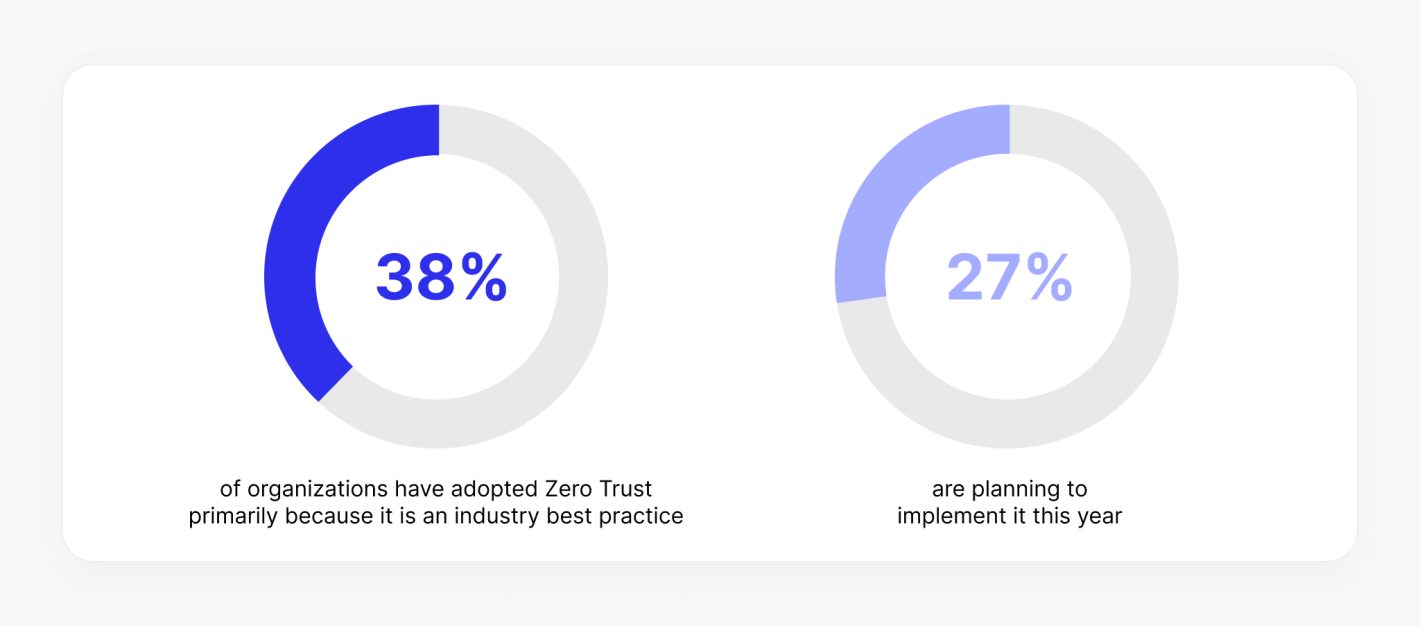
Source: Statista
Enterprises are leveraging Zero Trust to confidently embrace cloud services, remote work, and emerging technologies without increasing exposure to cyber threats. Traditional VPNs, for example, are being replaced by Zero Trust Network Access (ZTNA), which provides secure, granular access to applications without exposing the broader network. Unlike VPNs, which create a broad attack surface, ZTNA makes applications invisible to unauthorized users and dynamically adjusts permissions based on risk signals.
Cloud-native Zero Trust – often integrated into Secure Access Service Edge architectures — also simplifies IT environments by consolidating security controls. Instead of juggling disparate firewalls, VPNs, and endpoint protection tools, organizations can streamline their security stack while improving scalability.
The market is taking note. Analysts project that the global Zero Trust security market will grow from $32 billion in 2023 to $133 billion by 2032, driven by widespread enterprise adoption. Companies that implement Zero Trust aren’t just avoiding breaches — they’re achieving operational efficiencies. Ultimately, Zero Trust aligns security with business outcomes.
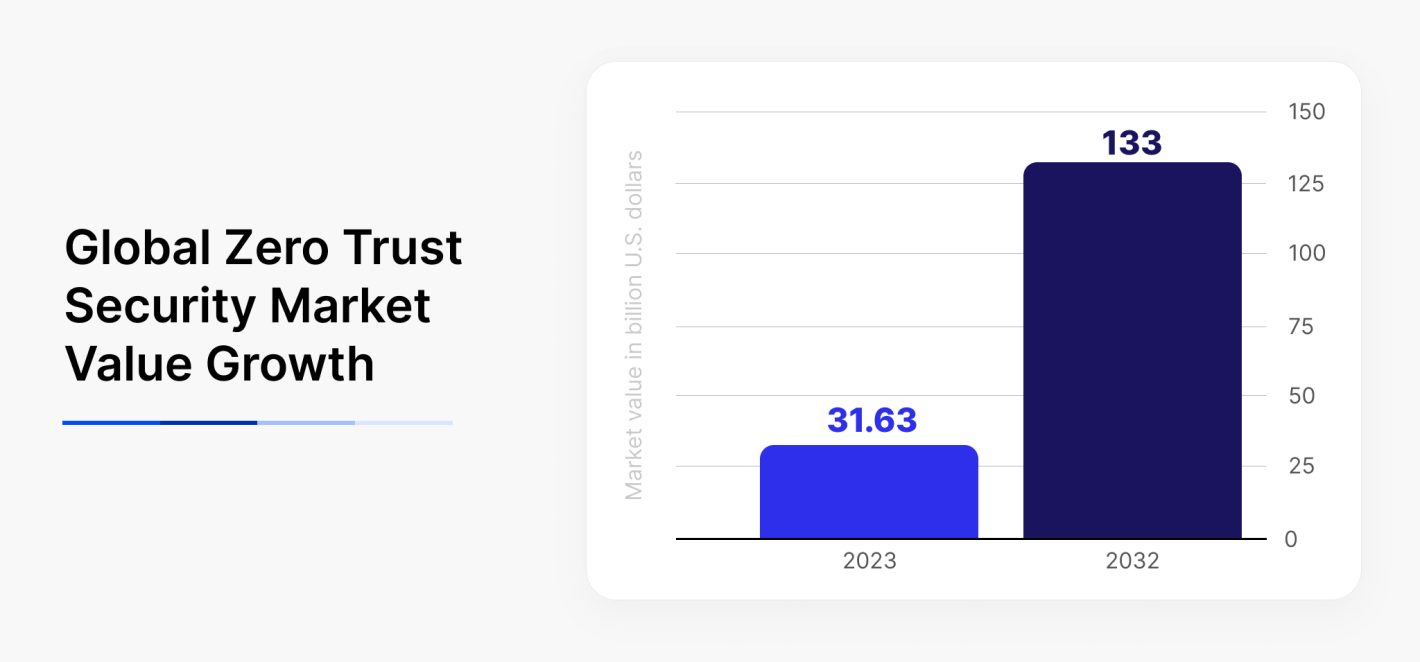
Source: Statista
The Intersection of Security and Modernization
As our practices in Sombra show, ZTA comes in hand with such niches as App modernization as well. Zero Trust Architecture ensures that security does not hinder innovation. By removing implicit trust and enforcing continuous verification, ZTA secures modern applications while enabling faster, more secure cloud adoption. Here are some use cases of ZTA that we leverage during our Modernization projects
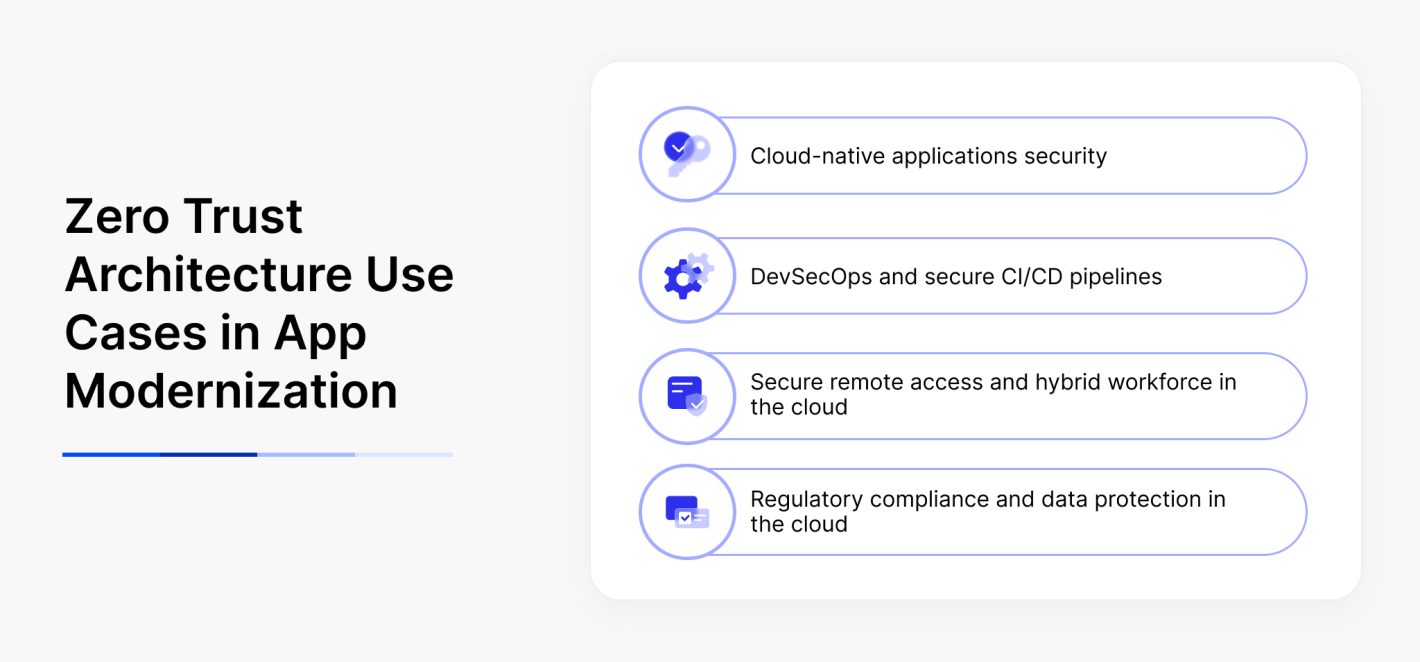
Main Zero Trust architecture use cases
Cloud-Native Applications Security
- Microservices and containerized applications are designed for scalability but can introduce security gaps. ZTA implements identity-based access controls, ensuring that only verified services and users can communicate within cloud environments.
- Micro-segmentation and API security restrict unauthorized access, preventing attackers from exploiting vulnerabilities in one microservice to compromise an entire application.
DevSecOps & Secure CI/CD Pipelines
- Traditional DevOps prioritizes speed, but security must be embedded into the Continuous Integration/Continuous Deployment (CI/CD) pipeline to prevent vulnerabilities from entering production.
- ZTA enforces just-in-time, least-privilege access for developers, automates security testing at every build stage, and ensures code integrity from development to deployment.
Secure Remote Access & Hybrid Workforce in the Cloud
- With remote teams and hybrid workforces becoming the norm, traditional VPN-based security is inadequate. Zero Trust Network Access (ZTNA) replaces VPNs with context-aware authentication, granting employees secure access to applications without exposing entire networks.
- Continuous monitoring ensures that user behavior aligns with expected activity — if a login attempt is flagged as unusual (e.g., unexpected geolocation), access is automatically restricted or revoked.
Regulatory Compliance & Data Protection in the Cloud
- Many industries, including finance, healthcare, and retail, require strict compliance with regulations like GDPR, HIPAA, and PCI-DSS. ZTA facilitates compliance by providing:
- Granular access controls to protect sensitive customer data.
- Audit logs and real-time monitoring to detect and respond to unauthorized access attempts.
- Encryption by default, ensuring data remains secure in transit and at rest.
Zero Trust in Action: Case Studies Across Industries
Technology: How Google Secured Its Workforce
Google’s BeyondCorp initiative is perhaps the most well-known Zero Trust case study. After state-sponsored hackers targeted the company in 2009, Google abandoned the concept of a trusted corporate network. Instead, employees now authenticate to applications directly over the internet, with access determined dynamically based on device health, identity, and risk. This shift eliminated VPNs, streamlined remote work, and significantly improved security.
Financial Services: Banks Fortify Digital Transactions
Financial institutions were among the earliest adopters of Zero Trust due to the sensitive nature of banking data. A leading African bank, for example, implemented a Zero Trust framework to secure its branch networks and remote employees. By enforcing strict identity verification and micro-segmentation, the bank reduced security vulnerabilities while ensuring compliance with financial regulations.
Global giants like JPMorgan Chase have followed suit, integrating Zero Trust principles into their cybersecurity strategies to combat advanced threats. Meanwhile, investment banks are leveraging identity-based access controls to prevent unauthorized trading and data leaks.
Healthcare: Protecting Patient Data and Medical Devices
Hospitals and healthcare providers are increasingly turning to Zero Trust to safeguard electronic health records and connected medical devices. Cyberattacks on hospitals can have life-threatening consequences, making security a top priority.
A regional hospital network established Zero Trust segmentation to separate clinical devices, such as MRI machines and IV pumps, from general hospital systems. This approach effectively prevented malware from spreading throughout the network, ensuring that a single compromised device would not jeopardize essential medical infrastructure.
As HIPAA and other healthcare regulations tighten security requirements, Zero Trust has become essential for protecting patient data. The approach has also facilitated secure telemedicine adoption by ensuring that doctors and patients can interact safely from remote locations.
Government: Mandating Zero Trust for National Security
Governments worldwide are enforcing Zero Trust to protect against cyber espionage and state-sponsored attacks. In 2021, the U.S. government mandated that all federal agencies implement Zero Trust by the end of FY 2024. This includes requirements such as enforcing multi-factor authentication, encrypting all internal traffic, and logging every access request.
The Department of Defense is taking the lead with a Zero Trust roadmap, with plans for full implementation by 2027. This initiative aims to prevent any adversary, whether foreign or domestic, from exploiting implicit trust in government systems. Other countries, including the UK and Australia, are adopting similar strategies to secure their public sector networks.
Manufacturing & Critical Infrastructure: Preventing Sabotage
Historically, manufacturing and energy sectors relied on air-gapped networks to protect industrial systems. But with the rise of Industry 4.0 and IoT, those networks are now interconnected with cloud environments — introducing new risks.
For instance, one automotive manufacturer implemented Zero Trust segmentation in its factories, ensuring that production machines could only communicate with authorized services. This prevented malware outbreaks that previously could have shut down entire assembly lines. Similarly, energy companies are deploying Zero Trust to protect power grids from cyberattacks. If a hacker gains access to a corporate IT system, Zero Trust ensures they cannot directly control critical infrastructure without passing multiple layers of authentication and verification.
Implementing Zero Trust: A Roadmap for Executives
Adopting Zero Trust is a long-term transformation, not a quick fix. Here’s a practical roadmap for enterprise leaders looking to implement Zero Trust successfully:
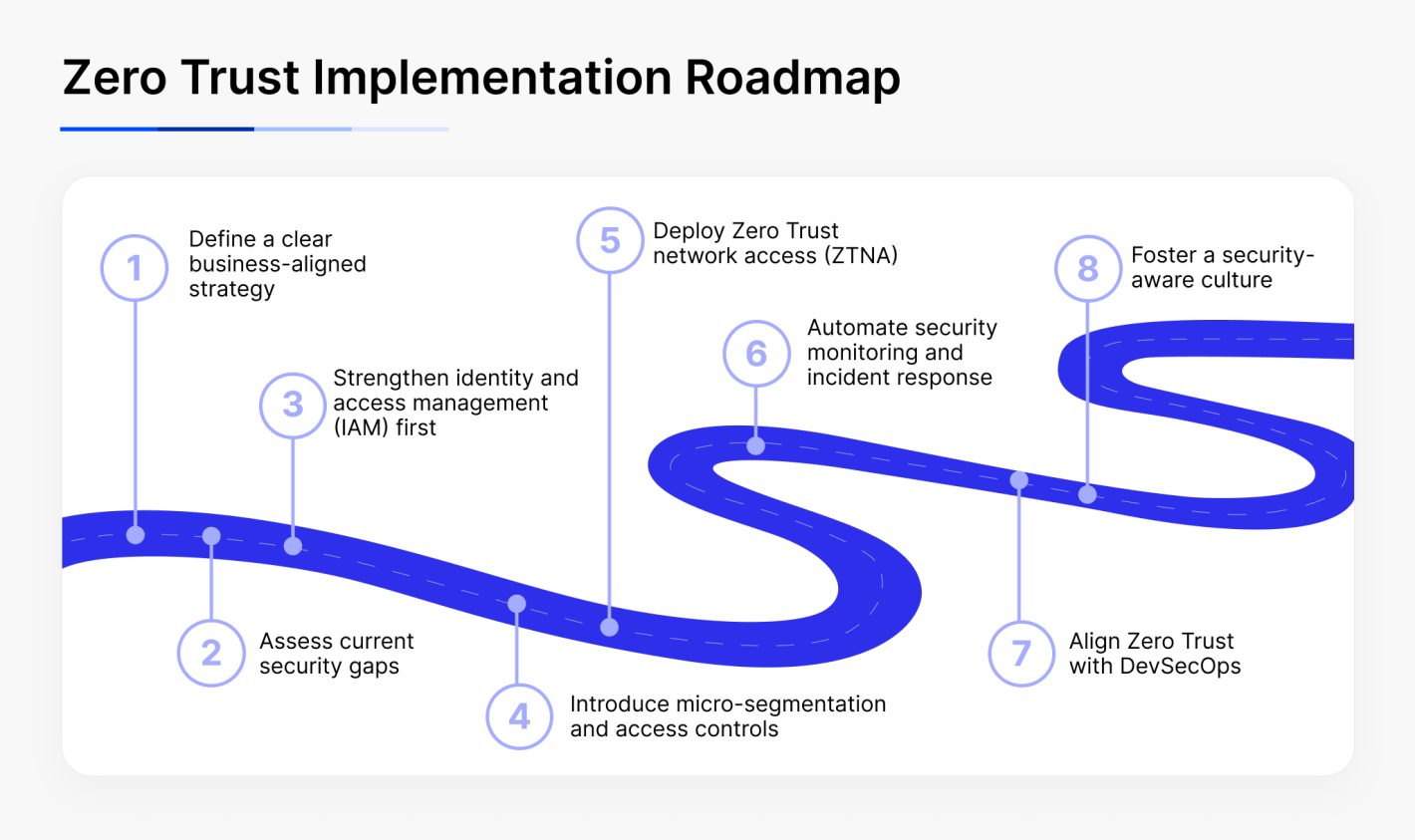
Zero Trust implementation roadmap for executives
1. Define a Clear Business-Aligned Strategy
Executives should start by framing Zero Trust as a business enabler, not just a security initiative. Identify critical assets — customer data, intellectual property, cloud workloads—that require the highest level of protection. Tie Zero Trust implementation to strategic goals, such as secure cloud adoption, remote workforce enablement, or regulatory compliance.
2. Assess Current Security Gaps
Conduct a Zero Trust maturity assessment to map out existing security weaknesses. Identify where implicit trust still exists — such as overprivileged accounts, unprotected SaaS applications, or open internal network segments. This assessment helps prioritize areas where Zero Trust will deliver the highest impact.
3. Strengthen Identity and Access Management (IAM) First
Zero Trust starts with identity. Organizations should:
- Enforce Multi-Factor Authentication (MFA) for all users, especially privileged accounts.
- Implement Single Sign-On (SSO) to streamline authentication.
- Remove privileged accounts, ensuring users only access what they need.
- Monitor and audit identity access logs continuously to detect anomalies.
4. Introduce Micro-Segmentation and Access Controls
Segment the network so that each department, application, or service operates in isolation. Use firewalls, cloud security groups, and software-defined perimeters to enforce access policies. Encrypt all internal traffic to prevent unauthorized data interception.
5. Deploy Zero Trust Network Access (ZTNA)
ZTNA replaces traditional VPNs with identity-based access to specific applications. Unlike VPNs, ZTNA doesn’t grant broad network access—users can only connect to explicitly approved resources, reducing lateral attack movement.
6. Automate Security Monitoring and Incident Response
Utilize AI-driven analytics to continuously evaluate risk signals—login behaviors, device compliance, and network flows—and automatically revoke access when anomalies are detected. Implement Security Information and Event Management (SIEM) systems to collect and analyze Zero Trust security data in real-time.
7. Align Zero Trust with DevSecOps
Ensure that all new applications follow Zero Trust principles by design:
- Require authentication for all API calls (even between internal services).
- Use automated infrastructure-as-code to enforce security policies.
- Scan for vulnerabilities before deployment in DevOps pipelines.
8. Foster a Security-Aware Culture
Zero Trust succeeds only when employees, developers, and executives understand its value. Provide training and change management programs to ensure smooth adoption. Encourage feedback to balance security with usability, avoiding unnecessary friction.

Are You Ready for Zero Trust?
As cyber threats grow more sophisticated, organizations can no longer rely on outdated security models that assume trust. By embracing Zero Trust, enterprises can do a lot more regarding their security and more.
At Sombra, we help businesses secure modern applications while accelerating cloud adoption. Our expertise spans infrastructure security, cloud-native application protection, and secure software delivery, ensuring that security is embedded from development to deployment. This means:
- End-to-End Security – We implement Zero Trust controls across your IT landscape, from identity and access management to secure cloud environments.
- Automated CI/CD Security – Our DevSecOps frameworks integrate continuous security testing, vulnerability scanning, and compliance automation into your development pipeline.
- Micro-Segmentation & API Security – We prevent lateral movement with fine-grained access controls, encryption, and behavior-based threat detection.
- Cloud-Native Protection – Whether you’re running AWS, Azure, or hybrid cloud architectures, our team secures your workloads without slowing down development cycles.
- Regulatory Compliance Support – We help businesses meet GDPR, HIPAA, SOC 2, and other industry standards, ensuring full compliance with security best practices.
And that’s not all! If you want to understand the benefits specifically for your organization, let’s talk! But remember one thing — isn’t something to skimp on.











