Cybercrime is on the rise. An ever-changing digital landscape keeps on challenging business leaders. By 2025, the cybercrime cost is predicted to reach $10.5 trillion annually.
Data remains the primary target for a cyber attack. In 2020, the U.N. reported a 600% increase in malicious emails during the COVID-19 pandemic. Russia’s unprovoked and unjustified military aggression against Ukraine poses a more serious cybersecurity threat worldwide. Over the past several months, the CERT-UA cybersecurity team recorded hundreds of cyberattacks on the country’s critical information infrastructure and public organizations.
The number of attack attempts will keep on growing. Business leaders need to react fast to avoid information leakage or vital business process disruption. Therefore, a cybersecurity plan must be developed with business objectives in mind.
In 2022, C-level managers of eight in ten UK businesses report that cyber security is a high priority.
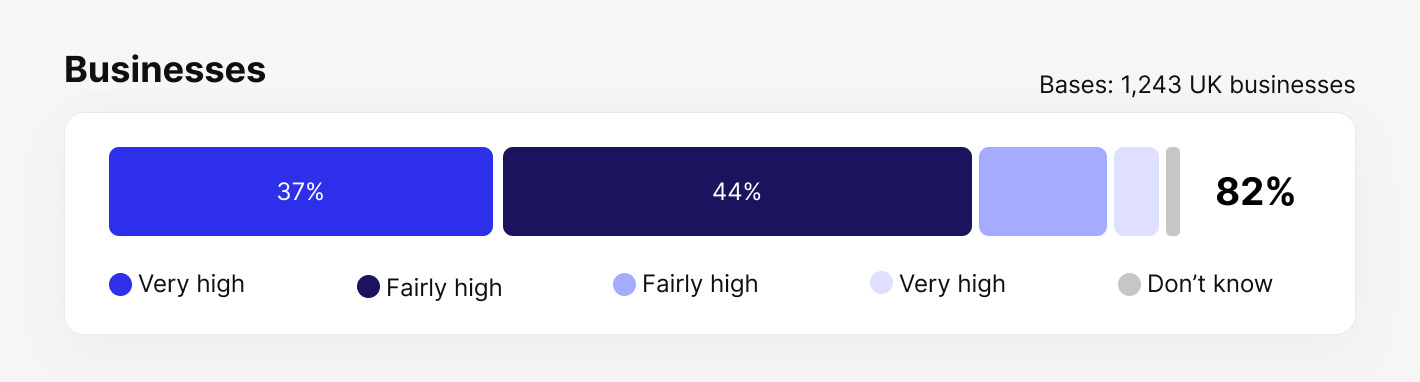
Extent to which cyber security is seen as high or low priority for directors, trustees, and other managers, based on 1243 UK businesses.
Around 55% of medium businesses outsource their IT and cyber security to an internal supplier.
As a company that provides software development and consulting services, Sombra ensures to meet our clients’ information security expectations.
Secure IT outsourcing: risks and responsibilities
IT outsourcing is an excellent solution for mid-sized companies to access greater expertise, resources, and cybersecurity standards. Yet, outsourcing IT needs still carries risks to a business’s cybersecurity. It can expose businesses to unauthorized access, weak monitoring, and compliance gaps.
As a software engineering and AI consulting company, Sombra builds, develops, modernizes, and provides consulting services for products, technologies, and IT challenges of all kinds, while adhering to the latest security frameworks, including ISO 27001. This ensures that information security is embedded into our delivery processes. Thus, you should build security into your architecture and delivery instead of audits.
To manage the outsourcing risks effectively, business leaders must take a structured, proactive approach.
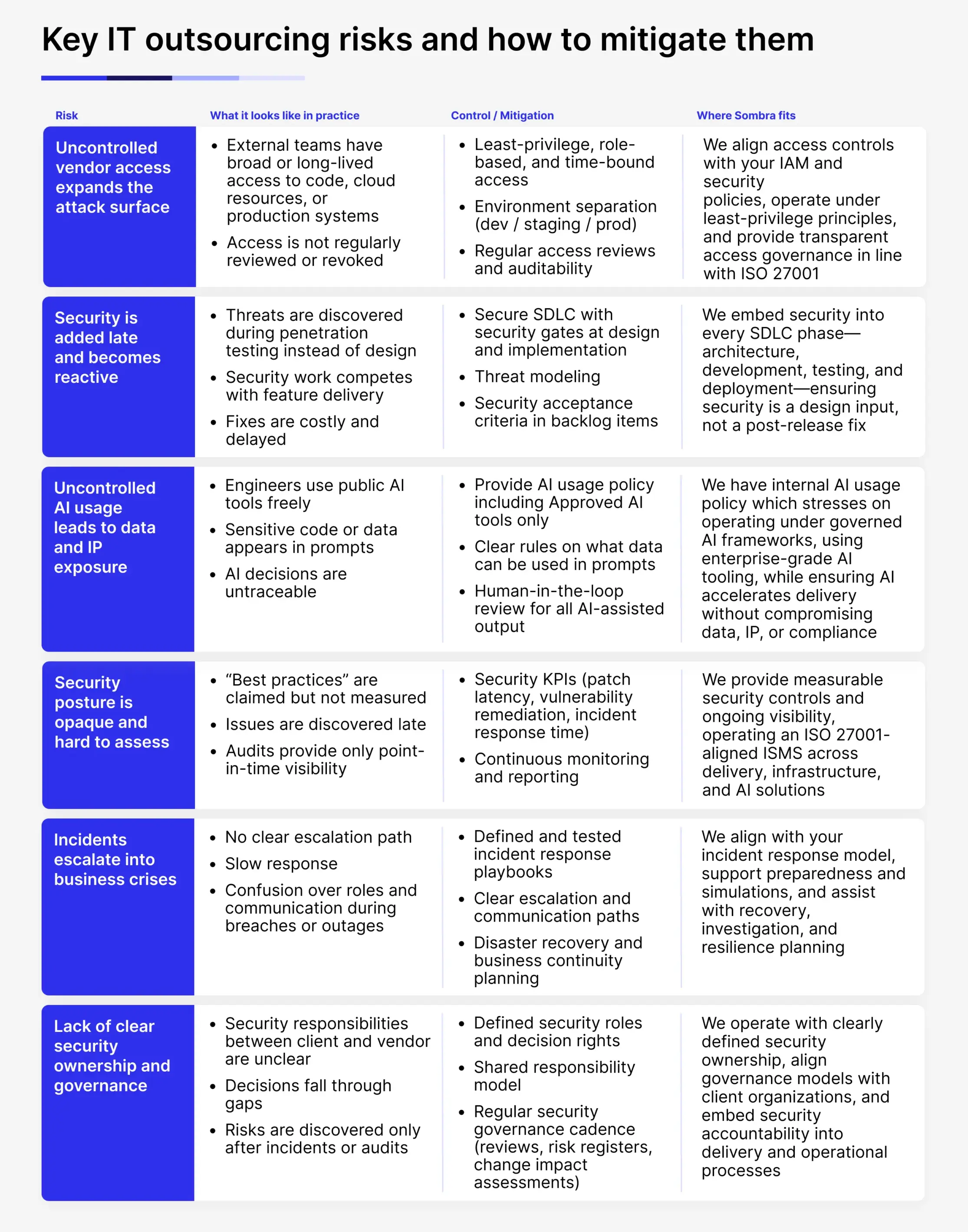
Six security risks in IT outsourcing
Uncontrolled vendor access expands the attack surface
An expansion of the attack surface happens access when to an organization’s resources isn’t regularly reviewed or revoked. Thus, external teams can have broad or long-lived access to code, cloud resources, or production systems.
Mitigate this risk with Sombra
You can control or reduce the risk through
- least-privilege, role-based, and time-bound access;
- environment separation (dev / staging / prod);
- regular access reviews and auditability.
When working with clients, we align access controls with their IAM and security policies, operate under least-privilege principles, and provide transparent access governance in line with ISO 27001.
Security is added late and becomes reactive
When security is not built into architecture and delivery from day one, threats can be discovered during the penetration testing instead of design. This leads to security work competing with feature delivery resulting in costly fixes and product/feature release delays.
Mitigate this risk with Sombra
You have to secure the SDLC with
- security gates at design and implementation;
- threat modeling;
- security acceptance criteria in backlog items.
At Sombra, we embed security into every SDLC phase: architecture, development, testing, and deployment, ensuring security is a design input instead of a post-release fix.
Uncontrolled AI usage leads to data and IP exposure
AI usage governance should be treated as a first-class security problem, since engineers use public AI tools freely, sensitive code or data can appear in prompts. On top of that, AI decisions are untraceable.
Mitigate this risk with Sombra
Generally speaking, you should provide an AI usage policy including
- approved AI tools only;
- clear rules on what data can be used in prompts;
- human-in-the-loop review for all AI-assisted output.
We’ve developed an internal AI usage policy which stresses on operating under governed AI frameworks, using enterprise-grade AI tooling, while ensuring AI accelerates delivery without compromising data, IP, or compliance.
Security posture is opaque and hard to assess
When security relies on claimed “best practices” instead of measurable controls, visibility is limited. Issues are often discovered late, and audits provide only point-in-time snapshots rather than continuous assurance. This makes it difficult for organizations to understand their true security posture or identify emerging risks early.
Mitigate this risk with Sombra
You should make security measurable and continuously visible through
- security KPIs (patch latency, vulnerability remediation, incident response time);
- continuous monitoring and reporting.
At Sombra, we provide measurable security controls and ongoing visibility, operating an ISO 27001-aligned ISMS across delivery, infrastructure, and AI solutions to ensure security posture is continuously assessed.
Incidents escalate into business crises
Without a clear escalation path, security incidents and outages can quickly spiral into business-level crises. Slow response times, unclear roles, and breakdowns in communication during incidents increase operational disruption and prolong recovery.
Mitigate this risk with Sombra
You should plan for failure with proven response and continuity readiness, including
- defined and tested incident response playbooks;
- clear escalation and communication paths;
- disaster recovery and business continuity planning.
We align with your incident response model, support preparedness and simulation exercises, and assist with recovery, investigation, and resilience planning, helping contain incidents before they impact the business.
Lack of clear security ownership and governance
When security responsibilities between client and vendor are unclear, decisions fall through organizational gaps. Risks may go unmanaged and only surface after incidents or during audits, increasing exposure and accountability challenges.
Mitigate this risk with Sombra
You should establish clear security ownership and governance across organizations through
- defined security roles and decision rights;
- a shared responsibility model;
- regular security governance cadence (reviews, risk registers, change impact assessments).
In our work, we operate with clearly defined security ownership, align governance models with client organizations, and embed security accountability into delivery and operational processes to ensure risks are actively managed.
6 rules to reduce cybersecurity risk when outsourcing IT
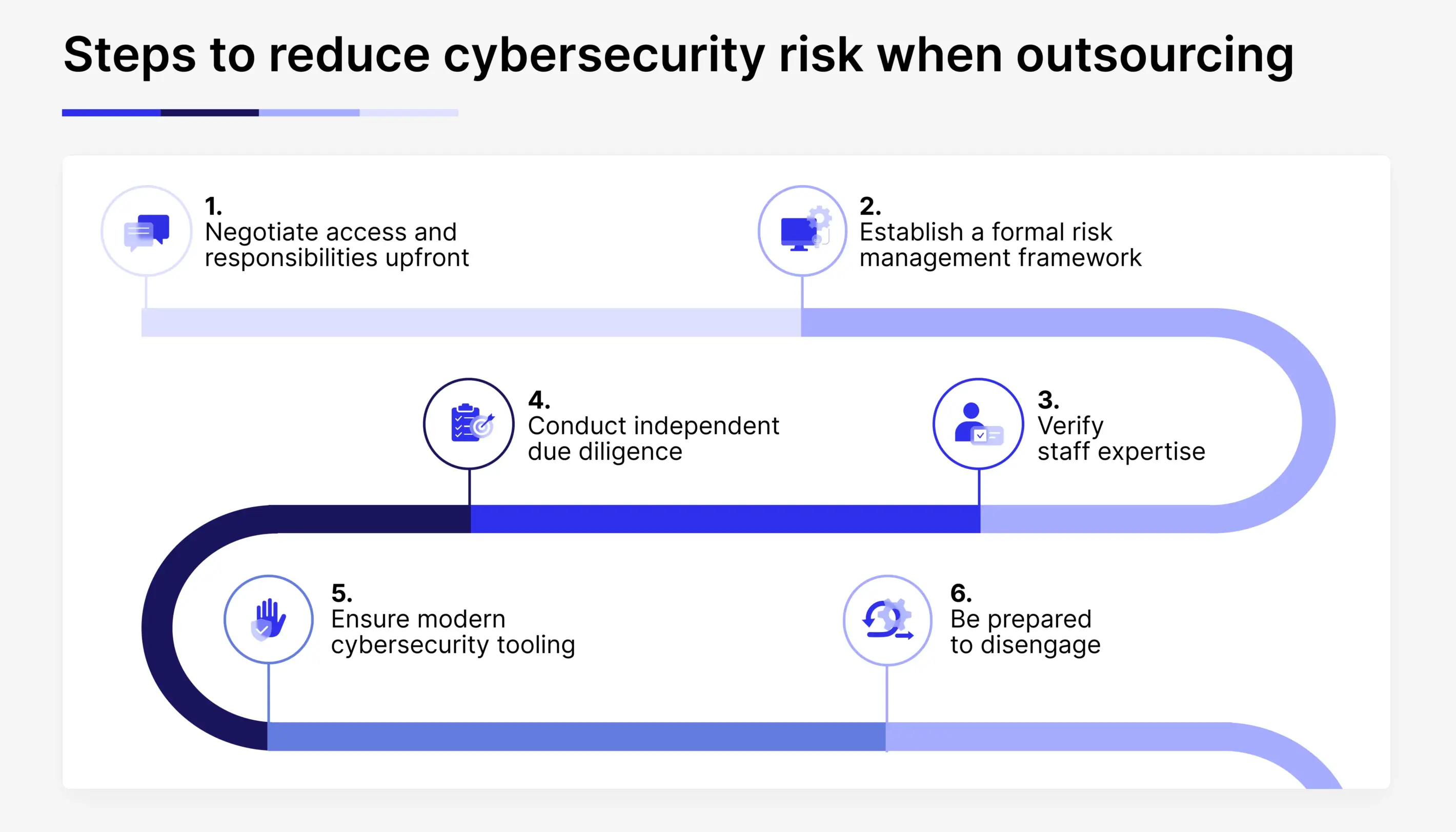
Negotiate access and responsibilities upfront
Outsourcing contracts should clearly define what systems and data a third party can access. Grant only the minimum level of access required to deliver services effectively. Full administrative privileges should never be assumed.
Establish a formal risk management framework
Ensure your IT outsourcing partner has implemented an information security management system (ISMS) aligned with ISO/IEC 27001. This internationally recognized standard demonstrates a commitment to managing and protecting sensitive information. An effective ISMS enables organizations to identify security risks, establish and monitor controls, set measurable objectives, and drive continuous improvement in security practices.
Verify staff expertise
One of the most overlooked outsourcing risks is the lack of technical or security expertise. Review the vendor’s case studies, certifications, and the conditions for delivery models they offer. A reputable partner like Sombra demonstrates security maturity across the entire organization.
Conduct independent due diligence
Outsourcing shouldn’t eliminate accountability. Independent audits, security assessments, and regular reviews help ensure that a third-party vendor’s practices remain aligned with your risk tolerance.
Ensure modern cybersecurity tooling
Effective cybersecurity relies on up-to-date solutions, including next-generation firewalls (NGFW), next-generation antivirus (NGAV), vulnerability management, secure backups, and disaster recovery capabilities. These tools support information, operational, and network security across environments.
Be prepared to disengage
If a third-party software development provider cannot meet your cybersecurity expectations or respond adequately to incidents, leadership must be prepared to reconsider the partnership. Security misalignment is a valid reason to walk away.
SMB checklist for secure IT outsourcing
Considering the risks and rules we’ve mentioned previously, here a checklist you can use when starting a cooperation with a software development vendor.
- Confirm your outsourcing partner operates under a formal security management system (e.g., ISO 27001 or equivalent).
- Treat the vendor as part of your security perimeter and enforce least-privilege, time-bound access.
- Require security to be built into system design and delivery, not added later.
- Ensure AI tools used by the vendor are approved, governed, and restricted from exposing sensitive data or IP.
- Establish clear security ownership and decision-making across both organizations.
- Demand measurable security controls and continuous visibility, not annual assurances.
- Enforce strict separation between development, staging, and production environments.
- Require documented and tested incident response and escalation procedures.
- Verify that secure coding standards and reviews are applied to all delivered software.
- Include security obligations, audit rights, and exit requirements in all outsourcing contracts.
Summary
According to common threat intelligence reports, today’s most prevalent cyberattacks include email compromise, phishing, supply chain attacks, vulnerability exploitation, ransomware, malware, man-in-the-middle attacks, cross-site scripting (XSS), SQL injection, password attacks, and IoT-based threats.
For mid-sized businesses, outsourcing IT services can significantly improve security and resilience when the best practices are applied. This starts with clear access controls, structured risk management, careful vendor selection, and continuous oversight.
By partnering with an experienced IT outsourcing provider like Sombra, you can securely scale technology capabilities while maintaining control, compliance, and confidence.
If you’re looking to outsource IT securely and responsibly, and get things done right, Sombra can help design a solution that delivers real business value.
Contact us to discuss your business needs.











